
We are a select team of highly-experienced cyber professionals offering expert consultation and implementation of cyber solutions. We take great pride in being able to offer innovative and robust solutions at competitive rates.
Most technology companies are simply “integrators” who buy off-the-shelf commercial technology and install it within your organization without a thorough understanding of how the solutions operate under-the-hood. This business model usually results in both high prices and low security.
We are doers, not buyers.
“Integrators” need to charge a mark-up on-top of what their big-box suppliers are charging. As a result of these premiums, your price inflates with each company in the chain. A lack of thorough understanding of these third-party, off-the-shelf solutions often results in weak security considerations and vulnerable implementations leading to a playground for hackers.
We take a grass-roots approach; erring towards open-source “tried-and-true” solutions with customized configurations but non-custom components. License management is a nightmare for many organizations - integrators purchase licenses during the initial setup (often at a discount) then leave organizations to deal with an annual onslaught of purchasing requirements and license key updates to deploy. Open-source solutions alleviate this headache by removing licensing requirements altogether. Why doesn’t everyone do this? Because it requires expertise that average technology providers simply don’t have.

Configure, don’t code.
Custom solutions require custom support. Every line of code written has a cost to maintain while every line of configuration written is maintained by the developer. It’s our goal not to lock you into our services by providing you with a custom solution that is only supportable by a specific company. By sticking to industry-standard open-source solutions, our customers can hire any firm with open-source expertise to maintain or service our products in the future. We stand behind our skills, but encourage customers to choose the firm that best fits their needs, even if that’s not us - we design our solutions to specifically support that.
We provide a default non-disclosure agreement as standard practice on all contracts and encourage customers to amend that agreement with their own custom text or have us sign their own. We’re in the business of protecting information, not selling it.
Many organizations just want solid advice in regard to what they need to implement their technological issues. A simple, but honest, analysis that provides a concise overview of options and expenses is critical for making smart and effective technological choices. Many smaller companies choose to implement these solutions on their own after a bit of advice from us. We’re in the business of providing knowledge and support, not in the business of trying to weasel monthly service contracts out of clients.

Very simply; a customer wants to be able to do something and we make it so they can. We do this somewhat contrary to industry norms. Most organizations ask for the requirements upfront, they build the product, and then hand it to the customer. We find this frequently results in frustrated customers. Most times, customers know what functionality they want but don’t understand the capabilities and limitations of the technology. Other companies might deliver what they consider to be a fully finished product according to customer requirements. However, during a lengthy development process, requirements can change or contradict each other, and the resulting product turns out to be not at all what the customer expected.
We approach this service iteratively. We provide the customer with an initial deployment of the capability with the smallest level of basic functionality. After some use, the customer provides feedback on changes and features they’d like to see in the next iteration. This workflow results in customers who get exactly what they want more efficiently than is more efficiently than is possible with an “all-the-requirements-upfront” approach.
Technology changes daily, with upgrades, vulnerabilities, and maintenance being a part of that evolution. We find the older a company’s infrastructure gets, the more it costs to maintain. We commonly implement the decommissioning & replacement of these legacy services. This process is usually a weight off the customer’s shoulders as we strive to ensure the replacement is low maintenance and bit-rot resistant. Continued support of antiquated services adds to a system’s long term maintenance costs, so it’s important to design the system to anticipate and minimize those future costs.
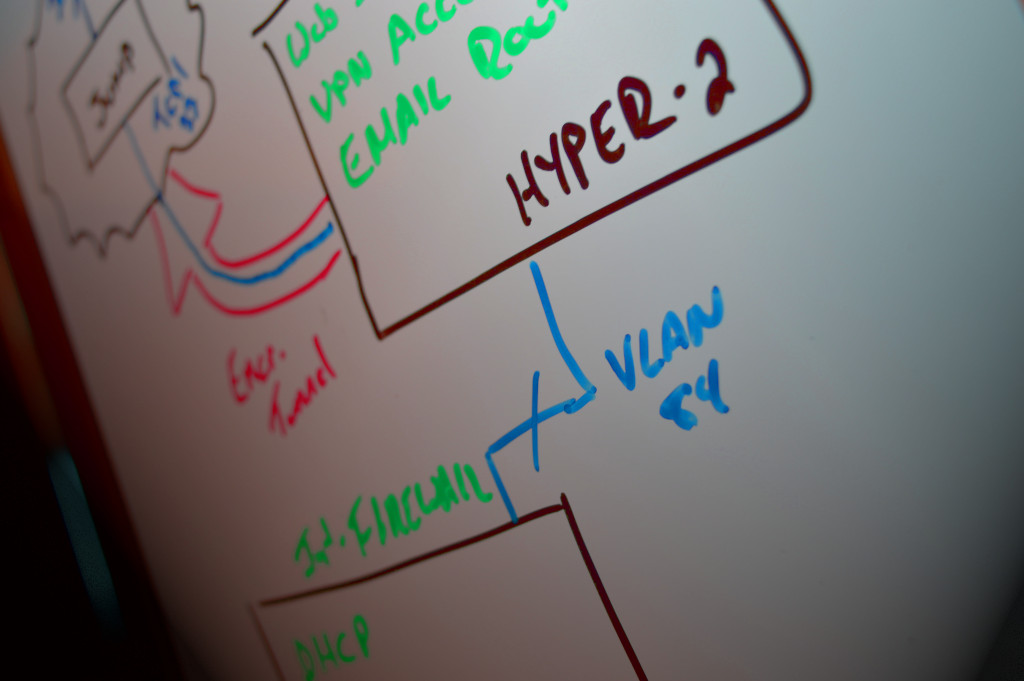
We do an inside-out approach to vulnerability assessments, determining vulnerable services via configuration and architecture analysis. Although we think it’s important to use classic pentesting techniques against public facing services, we find port scans and guess-and-check style assessment usually only catches low-hanging fruit.

We are adamant about proper network monitoring. Humans are inconsistent when it comes to boring and monotonous tasks. They neglect to review textual logs, they forget to run system diagnostics, and they forget to review net flow data for signs of intrusion - even if you are paying them to do so. The key is automation, effective dashboarding, and low-false positive active alerting; let the computers do the monitoring and have the humans make decisions.
This system aggregates data from multiple sources, each in their own format then normalizes each dataset into defined standards. These standard objects are ingested into a visualizer for easy overview consumption, while the irreplaceable original data is stored compressed and encrypted for later use or reprocessing.
Big Data Normalization and Processing
This system aggregates data from multiple sources, each in their own format then normalizes each dataset into defined standards. These standard objects are ingested into a visualizer for easy overview consumption, while the irreplaceable original data is stored compressed and encrypted for later use or reprocessing.
Zero-Trust Network Implementation
This drop-in solution sits between existing web services and end-users to allow authentication using a more secure password-less architecture that employs physical tokens. Web services are configured with dynamic ingress and egress networking rules that limit lateral movement in the event of compromise. Comprehensive logging is added to identify atypical behavior and isolate the problem at its source..
Portable Infrastructure Services
This project combines several virtual appliances to provide fully on-premise cloud infrastructure (“cloud at home”) offering a modular set of services such as routing, wireless access, authentication, logging, data synchronization and backup, and source control. With setup as easy as booting from a USB drive, this solution is the most portable network implementation you can find. Configurations are organically source controlled and can be easily tracked, secured, rolled-back, or shared and changes to the system are *non-persistent* so you are always running from a known state.
We’re organizing our source code; GitHubs are coming soon.

Lockstone Technologies LLC
8 The Green, Suite 4000
Dover, DE 19901
© 2022 Lockstone Technologies
All rights reserved